Table of Contents
Software as a Service (SaaS) offers an array of cost-effective and scalable solutions reshaping the way business operations get conducted. Catering and effectively redefining the multiple business dynamics, SaaS has steered a transformation with digital solutions.
But this booming SaaS industry has one of the biggest concerns- SaaS security.
As per the 2022 data released by Statista, 1802 cases related to data compromise have been reported in the United States. Data compromises, including data breaches, leakage, and exposure have affected over 422 million individuals in the same year.
Verizon’s data breach investigations report claims that 61% of data breaches happen due to compromised credentials. Unauthorized access, data leakage, cyber attack, and SaaS security posture management is the most concerning factor for SaaS providers.

SaaS Security Checklist
Get your free copy
Having a secure SaaS is the priority of the service providers but for that, they need to follow the best practices for SaaS security. It is crucial for them to have a watch on changing trends, evolving patterns of cyber attacks, changing tactics of data leakage, and stay ahead of the curve to provide uninterrupted and reliable service.
Before understanding the principles as well as the challenges and risks associated with SaaS security, let’s understand why SaaS security is of utmost importance.
Why is SaaS Security Important?
In the current digital ecosystem, SaaS security is crucial as businesses increasingly rely on Software as a Service applications for their daily business operations. Security breaches in SaaS applications can lead to devastating consequences, including data leaks, financial losses, legal consequences, and damage to a company’s reputation.
The need to protect sensitive data and ensure the uninterrupted flow of business processes needs to be the foremost priority. SaaS security is not just about safeguarding data; it’s about safeguarding the integrity of an organization and its ability to function securely.
SaaS security best practices encompass a diverse approach, from user education and access controls to encryption, monitoring, and proactive threat mitigation.
Moreover, with strict data protection regulations in place, non-compliance can result in penalties and legal consequences.
What are the Standard Principles for SaaS Security?
Securing Software as a Service (SaaS) applications and infrastructure is critical to protecting sensitive data and ensuring the trust of your users. However, different SaaS applications have unique architectures depending upon the nature of their features, tools, and industry needs.
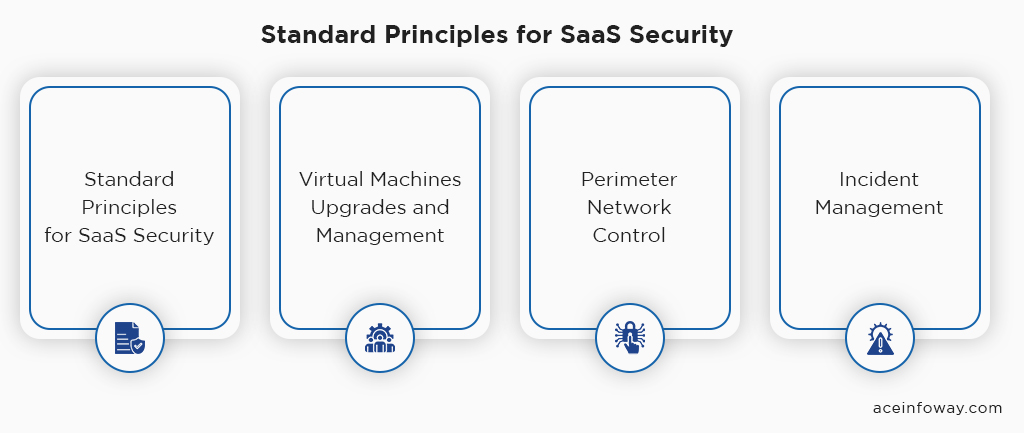
The principles for secure SaaS may vary depending on the product, here we are listing some standard principles you can practice for SaaS security.
Access Management:
- Authentication: Implement strong user authentication methods such as multi-factor authentication (MFA) to ensure only authorized individuals can access your SaaS application.
- Authorization: Define and enforce role-based access controls (RBAC) to limit user permissions based on their responsibilities.
- User Account Management: Regularly review and audit user accounts, ensuring that access is restricted for the employees who leave the organization.
Data Protection:
- Data Encryption: Encrypt data both in transit (using HTTPS) and at rest (using encryption keys) to safeguard sensitive information.
- Data Backup and Recovery: Regularly back up data and establish a robust data recovery plan to mitigate data loss in case of incidents.
Virtual Machines Upgrades and Management:
- Patch Management: Keep all virtual machines and underlying infrastructure up to date with security patches and updates to address vulnerabilities.
- Vulnerability Scanning: Conduct regular vulnerability assessments to identify and try to remove potential security weaknesses.
Reliability:
- High Availability: Design your SaaS application with limited and necessary elements only ensuring it remains accessible and operational even in the face of hardware or software failures.
Network Control:
- Firewalls: Implement network firewalls to control traffic and filter out destructive and doubtful requests.
- Network Monitoring: Continuously monitor network traffic to avoid any unfavorable incidents and potential security threats.
Perimeter Network Control:
- Perimeter Security: Establish strong perimeter security measures, such as intrusion detection and prevention systems (IDPS), to protect against external threats.
Incident Management:
- Incident Response Plan: Develop and regularly update an incident response plan that outlines the steps to take in the event of a security breach.
What are the Challenges and Risks Associated with SaaS Security?
Securing Software as a Service (SaaS) applications comes with various challenges and risks, primarily due to the nature of cloud-based, distributed systems and the probability of sensitive data exposure.
SaaS service providers cannot afford any loophole in SaaS security. Every SaaS product has different security challenges and risks, here we are listing a few of the common SaaS SaaS security challenges and risks:
 Lack of Control:
Lack of Control:
Organizations often have limited control over the underlying infrastructure and security measures in a SaaS environment since they rely on the service provider’s infrastructure. The lack of control can make it challenging to enforce specific security policies and respond to emerging threats effectively.
 Identity Management:
Identity Management:
Managing user identities, access controls, and authentication across various SaaS applications can be complex. Weak or inconsistent identity management can lead to unauthorized access and increase the risk of data breaches that could compromise the SaaS security posture management.
 APIs Insecurity:
APIs Insecurity:
Many SaaS applications offer APIs for integration, which can introduce security vulnerabilities if not properly secured. Insecure APIs can be exploited by attackers to access sensitive data or perform unauthorized actions within the SaaS application.
 Third-Party Integration:
Third-Party Integration:
Integrating multiple third-party services with SaaS applications can create security challenges, as each service may have different security standards and practices. Integration points can become weak links in your security facility that could lead to data breaches or unauthorized access.
 Misconfiguration:
Misconfiguration:
Incorrectly configured settings in SaaS applications, such as access controls or permissions, can lead to vulnerabilities in SaaS security making it challenging to provide secure SaaS to the users.
 Consistent Monitoring:
Consistent Monitoring:
Maintaining continuous monitoring across multiple SaaS applications can be logistically challenging. Inadequate monitoring can result in delayed detection of security threats, allowing attackers to operate undetected for prolonged periods.
 Data Storage:
Data Storage:
SaaS providers store data in the cloud, often in multiple locations, which can raise concerns about data residency and sovereignty. Data stored in the cloud may be subject to different regulatory requirements and could be accessed by unauthorized parties if not adequately protected.
 Data Breaches:
Data Breaches:
SaaS applications can be targeted by attackers seeking to steal sensitive data if SaaS security posture management is not done properly. Data breaches can result in financial losses, reputational damage, and legal consequences.One of the most significant risks is unauthorized access to sensitive data stored in the cloud. Weak authentication, poor access controls, or compromised user credentials can lead to data breaches.
 Disaster Recovery:
Disaster Recovery:
Disasters are unpredictable and can happen anytime, regardless of ensuring all security measures and precautions are up-to-date and working fine. Hence, SaaS businesses should clearly know what happens to their data stored on the cloud servers in case of disasters. Implementing an efficient disaster recovery plan will help recover all your important data files and user information if natural disasters or accidental system failures occur.
 Regulatory Compliance:
Regulatory Compliance:
Organizations must ensure that they comply with various data protection and privacy regulations, which can vary by region and industry because non-compliance can lead to hefty fines and legal penalties as well as unfavorable consequences.For any SaaS business to thrive, its offerings must align with the necessary regulatory standards, including GDPR, HIPAA, SOX, and more. Furthermore, it’s prudent to verify whether your SaaS service providers possess security certifications such as ISO, ITL, and other relevant credentials.
How to Mitigate Challenges and Risks Related to SaaS Security?
To address these challenges and mitigate these risks, organizations should follow the below-listed measures to curb them:
- Implement strong identity and access management practices.
- Regularly assess and monitor their SaaS environment for vulnerabilities and misconfigurations.
- Encrypt data at rest and in transit.
- Develop a comprehensive incident response plan.
- Educate employees on security best practices.
- Collaborate with trusted SaaS providers with solid security measures.
- Conduct third-party security assessments for integrated services.
- Stay updated on relevant compliance requirements and ensure adherence.
What Are The Best Measures to Strengthen SaaS Security?
SaaS security is an ongoing process that requires vigilance, proactive measures, and continuous improvement to protect sensitive data and maintain user trust.

SaaS security is an ongoing process that requires vigilance, proactive measures, and continuous improvement to protect sensitive data and maintain user trust.
Data Encryption:
- Encrypt data both in transit (using protocols like HTTPS) and at rest (encrypting data stored in databases or on disk). Encryption helps protect data from unauthorized access.
Authentication and Authorization:
- Implement strong authentication methods, such as multi-factor authentication (MFA), to verify user identities.
- Use role-based access control (RBAC) to ensure that users only have access to the data and features necessary for their roles.
Secure Development Practices:
- Train your development team in secure coding practices, and conduct regular code reviews to identify and fix security vulnerabilities.
- Use secure coding frameworks and libraries to reduce common security risks.
Regular Software Updates:
- Keep all software components, including third-party libraries and frameworks, up to date to patch known vulnerabilities.
API Security:
- Secure APIs with proper authentication and authorization mechanisms.
- Implement rate limiting and throttling to prevent abuse of APIs.
Web Application Firewall (WAF):
- Deploy a WAF to filter and monitor HTTP requests to your application.
- It can help protect against common web-based attacks like SQL injection and cross-site scripting (XSS).
User Data Protection:
- Implement data masking and anonymization techniques to protect sensitive user data.
- Define clear data retention policies and regularly delete data that is no longer needed.
- Regularly backup critical data and test data recovery procedures.
- Ensure backups are encrypted and stored securely.
Third-Party Security Assessment:
- Assess the security practices of third-party vendors and partners you integrate with. Ensure they meet your security standards.
- Ensure compliance with relevant data protection laws and regulations (e.g., GDPR, HIPAA).
- Review the vendor’s security policies and procedures. Ensure they have documented security policies covering data protection, access control, incident response, and more.
Secure Infrastructure & Patch Management:
- Use a secure and well-maintained cloud infrastructure provider and configure security groups, firewalls, and access controls appropriately.
- Develop a process for promptly applying security patches and updates to your application and infrastructure.
Penetration Testing & Awareness:
- Conduct regular penetration testing and vulnerability assessments to identify and remediate security weaknesses.
- Provide resources and guidelines for your customers to enhance their own security when using your SaaS application.

SaaS Security Checklist
Get your free copy
Final Words
As the SaaS market continues to grow, a proactive and adaptable approach to SaaS security is crucial. It is essential to safeguard sensitive data, ensuring the integrity of these cloud-based solutions. Businesses must prioritize robust SaaS security measures to avoid data breaches and cyber-attacks. By conducting regular security assessments, investing in strong authentication and access controls, and adhering to data protection regulations, organizations can mitigate risks and have secure SaaS.
As an experienced and reliable SaaS development company, we follow stringent SaaS development processes and compliance to create a SaaS product for your business. If the security and performance of SaaS products are your concern and you are looking for a reliable as well as experienced SaaS developer contact us for assistance and consultancy.